Challenge 2 Haystack
Again, we are tasked with finding flags in a “.pcap” file; however, this time there are two flags.
First, open the file in WireshakPortable by double-clicking on the “WiresharkPortable.exe” file included in the CTFA “Programs” folder.
If presented with a warning, like the one below, click “Yes.”
Next, click on “File” in the upper right corner of the Wireshark application and select “Open.” Now navigate to where you saved the “Haystack.pcap” file and select it.
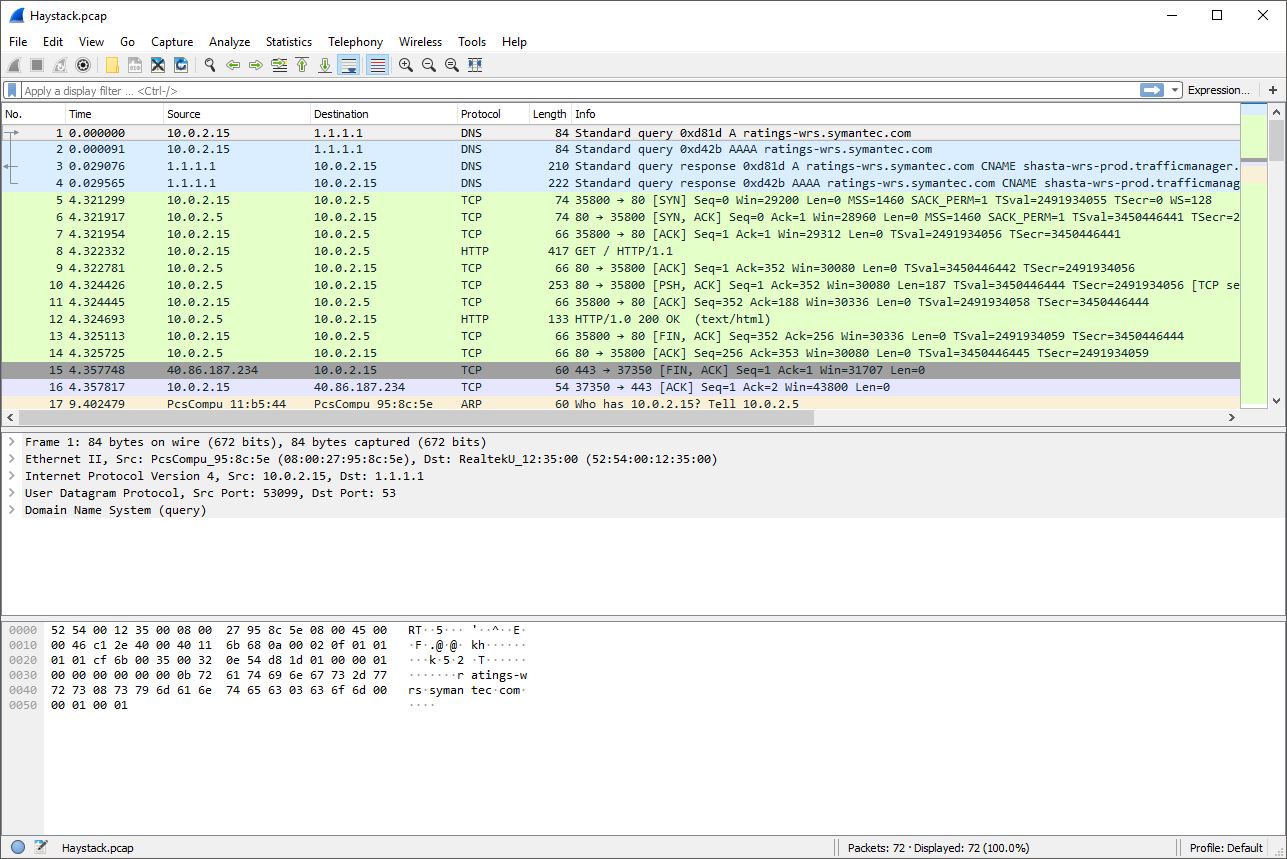
Now that the file is open, we can search for the flag. Unlike the last challenge, there are several different protocols captured in the file. Since we know the flag was on a webpage, we can start by looking through the “HTTP” packets. Analyzing the first HTTP response from the server, the second HTTP packet in the file, we can see the first flag. To get a better view, right-click the packet and select “Follow > TCP Stream.”
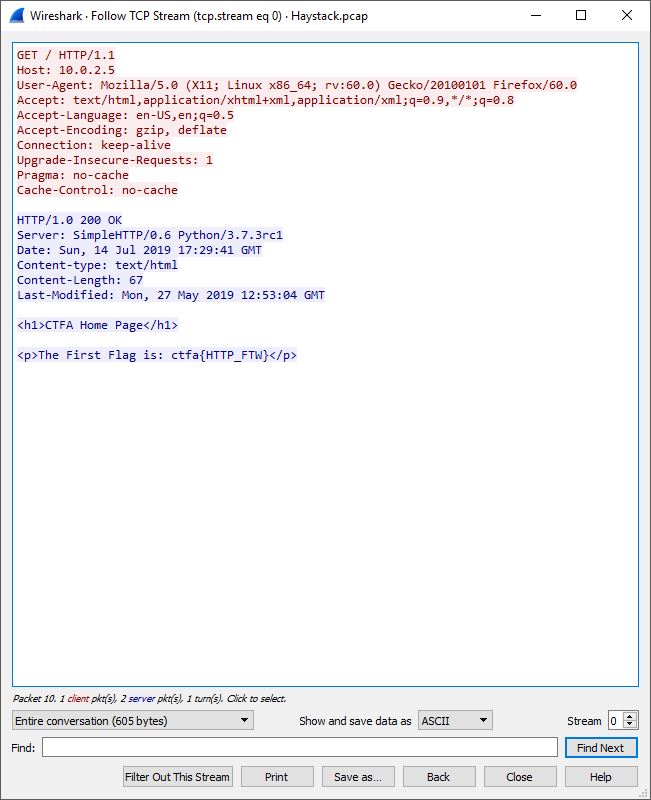
The first flag, ctfa{HTTP_FTW} can be seen in the picture above.
To resume analyzing the entire file, click the small “x” in the filter input bar.
To find the second flag, we will repeat the process of analyzing HTTP traffic for each page until we find the data containing the flag. In the last HTTP interaction, “/page4.html”, we will find the second flag.
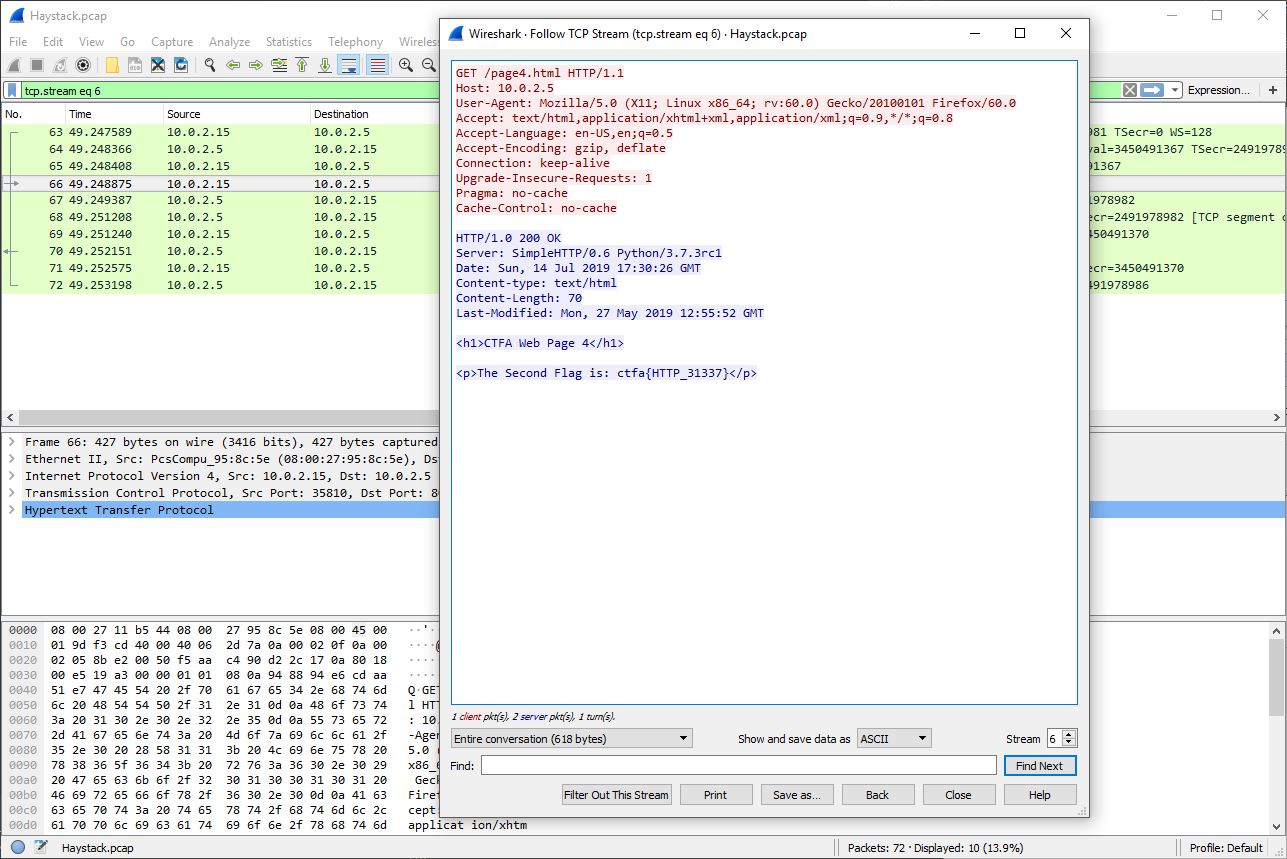
Great job! We now have both flags from this file.